As you would expect, the client is far easier to configure than the client. It will need the Certificate Authority certificate, its own certificate the associated private key, the TA key and some configuration.
The first connection I will make will be a point to point connection. By this I mean that the client will be assigned an IP address and be able to connect to the server as if it were on the local network. However all other traffic will not be affected – e.g. if I’m browsing the web then the traffic will got out to my ISP in the normal fashion. This type of connection is handy for when you want to connect home from a remote location, or you want to be able to us local network services without opening the firewall to let everyone to connect – so for example if you have a media serve and you want to use it when you are on the road this would be ideal.
The advantage of this type of connection is its simplicity. It will rely purely on the server and client configuration we have created, and doesn’t require additional firewall or routing updates. This phase is a stepping stone to the next phase when the client will route all traffic through the server, however, this phase will flush out errors with the keys, certificates and client/server communication. If this step doesn’t work, the more complex scenarios won’t either, and they will be far more difficult to debug.
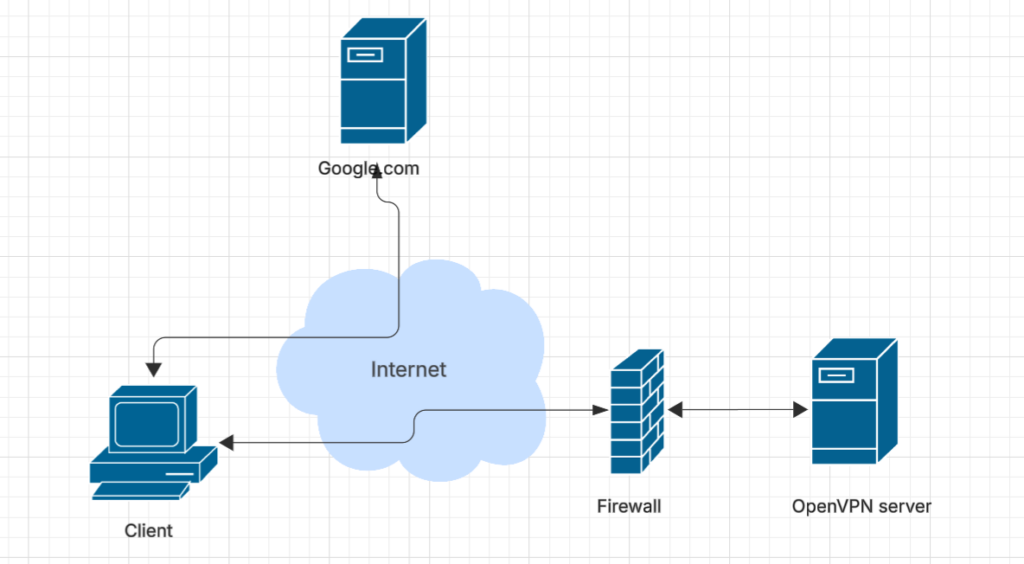
With this configuration the client will access the internet normally – its IP address will not be changed and it will use its regular DNS. However all traffic to the OpenVPN server subnet will be sent over the VPN.
This step is good for testing basic connectivity between the client and server, as well as the certificates and keys.
Client Certificates
Generate a certificate request as before – the client name is rizzo
john@ubuntu:~/easy-rsa$ ./easyrsa gen-req rizzo nopass
No Easy-RSA 'vars' configuration file exists!
Using SSL:
* openssl OpenSSL 3.0.13 30 Jan 2024 (Library: OpenSSL 3.0.13 30 Jan 2024)
......+.+......+.....+....+......+...+++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++*..+..+.........+.+......+.....+...+.........+...+....+..............+.+...+...+............+...+...+.....+.........+.+.....+.+...+..+...................+.........+..+......+....+...+..+......+...+....+.....+.+..+++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++*...+.......+.....+....+...+......+..+............+..........+.....+......+.......+.....+....+...+...+..+...+...+....+......+..+...................+........+...+....+........+...+..........+........+.+......+.....+...+.+.....+...+......+.......+..............+...+...............+.+..+....+........+++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++
.+.....+++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++*..........+.......+.....+.......+...+.....+...+...+.........+......+.+.....+.+.........+......+..+..........+++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++*.......+.+......+..+...+...+......+..........+.....+...............+...+...+.......+......+.........+......+..+.........+....+.....+............+..........+..+.+............+...+.................+...+.+.....+.+.....+.......+...+............+..+......+....+++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++
-----
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Common Name (eg: your user, host, or server name) [rizzo]:
Notice
------
Private-Key and Public-Certificate-Request files created.
Your files are:
* req: /home/john/easy-rsa/pki/reqs/rizzo.req
* key: /home/john/easy-rsa/pki/private/rizzo.keyAs before we get the Certificate Authority to sign the certificate.
john@ubuntu:~/easy-rsa$ ./easyrsa sign-req client rizzo
No Easy-RSA 'vars' configuration file exists!
Using SSL:
* openssl OpenSSL 3.0.13 30 Jan 2024 (Library: OpenSSL 3.0.13 30 Jan 2024)
You are about to sign the following certificate:
Please check over the details shown below for accuracy. Note that this request
has not been cryptographically verified. Please be sure it came from a trusted
source or that you have verified the request checksum with the sender.
Request subject, to be signed as a client certificate
for '825' days:
subject=
commonName = rizzo
Type the word 'yes' to continue, or any other input to abort.
Confirm request details: yes
Using configuration from /home/john/easy-rsa/pki/openssl-easyrsa.cnf
Enter pass phrase for /home/john/easy-rsa/pki/private/ca.key:
Check that the request matches the signature
Signature ok
The Subject's Distinguished Name is as follows
commonName :ASN.1 12:'rizzo'
Certificate is to be certified until Jun 4 15:45:52 2027 GMT (825 days)
Write out database with 1 new entries
Database updated
Notice
------
Certificate created at:
* /home/john/easy-rsa/pki/issued/rizzo.crtWe now have
- A private key located in /home/john/easy-rsa/pki/private/rizzo.key
- a certificate located in /home/john/easy-rsa/pki/issued/rizzo.crt
Client Configuration File
To keep things neat, I created a folder in my home directory to package everything together.
john@ubuntu:~$ mkdir openvpn_clients
john@ubuntu:~$ cd openvpn_clients/
john@ubuntu:~/openvpn_clients$ mkdir rizzoAs before, I copied a sample configuration file to get me started
john@ubuntu:~/openvpn_clients/rizzo$ cp /usr/share/doc/openvpn/examples/sample-config-files/client.conf .Editing this file there are a few key changes
Specify the server
;remote my-server-2 1194Specify the certificates and keys
ca ca.crt
cert rizzo.crt
key rizzo.keyNote: there is another way to do this by inlining the cryptographic information. I cover that on another page
Enable TLS
tls-auth ta.key 1There are a couple of things configured on the this line
- the TLS key – which is specified by ta.key
- the TLS key direction – which is either 0 or 1
Supporting Files
The client configuration refers to a few files (ca.crt, ta.key, rizzo.crt and rizzo.key) that need to be on the client machine. I copy them into the ~/openvpn_clients/rizzo folder
john@ubuntu:~/openvpn_clients/rizzo$ cp /home/john/easy-rsa/pki/issued/rizzo.crt .
john@ubuntu:~/openvpn_clients/rizzo$ cp /home/john/easy-rsa/pki/private/rizzo.key .
john@ubuntu:~/openvpn_clients/rizzo$ cp /home/john/easy-rsa/ta.key .
john@ubuntu:~/openvpn_clients/rizzo$ cp /home/john/easy-rsa/pki/ca.crt .checking they are all there, we can see
john@ubuntu:~/openvpn_clients/rizzo$ ls -l
total 24
-rw------- 1 john john 1184 Mar 1 16:01 ca.crt
-rw-r--r-- 1 john john 3446 Mar 1 16:03 ionos_client.conf
-rw------- 1 john john 4466 Mar 1 16:00 rizzo.crt
-rw------- 1 john john 1704 Mar 1 16:01 rizzo.key
-rw------- 1 john john 636 Mar 1 16:04 ta.keySetting up a Client
We now have all of the information required for connecting located in the openvpn_clients/rizzo directory. I simply tar it all up and copy it to the client machine.
On the client machine you need software to connect to the server. The OpenVPN client won’t work (yet) as we haven’t created the correct configuration file, so I use Tunnelblick
To get up and running with Tunnelblick, you drag and drop the client.conf file into the Tunnelblick window. Tunnelblick will then copy the configuration file, and all the files it references into a location managed by Tunnelblick. This is important to remember, because if you edit the original file it will have no impact whatsoever. In fact you can simply delete the files if you want.
To edit the configuration you now have to edit the file through Tunnelblick client.
Connect the Client
If everything has worked out so far, you will be able to create a point-to-point connection to the server.
In the client console you should see a bunch of log lines, and then it will finish with
2025-03-02 11:05:12.758632 MANAGEMENT: >STATE:1740913512,CONNECTED,SUCCESS,10.8.0.2,217.160.74.182,1194,,
2025-03-02 11:05:12.758656 Data Channel: cipher 'AES-256-GCM', peer-id: 0
2025-03-02 11:05:12.758667 Timers: ping 10, ping-restart 120
2025-03-02 11:05:12.758676 Protocol options: protocol-flags cc-exit tls-ekm dyn-tls-crypt
2025-03-02 11:05:13.869564 *Tunnelblick: Warning: DNS server address is not being used.
2025-03-02 11:05:13.877990 *Tunnelblick: Warning: DNS server address 192.168.1.254 is being used but should not be used. That may indicate that more than one network interface is active. Tunnelblick does not support multiple active network interfaces.
2025-03-02 11:05:19.236612 *Tunnelblick: This computer's apparent public IP address (x.x.x.x) was unchanged after the connection was madeThere are two important warnings
- DNS server address is not being used.
- his computer’s apparent public IP address (x.x.x.x) was unchanged
Given we haven’t set any DNS directives, and we are only setting up a point to point connection these are to be expected. In the next session I’ll tackle these.
On my Mac, I can see the connection is established, and I have an IP address of 10.8.0.2 – as per the CONNECTED,SUCCESS,10.8.0.2 portion of the log message
utun9: flags=8051<UP,POINTOPOINT,RUNNING,MULTICAST> mtu 1500
inet 10.8.0.2 --> 10.8.0.2 netmask 0xffffff00To test, I can connect over the VPN to the server using its local address of 10.8.0.1.
11:59:john@rizzo2:/Users/john ssh 10.8.0.1
Welcome to Ubuntu 24.04.2 LTS (GNU/Linux 6.8.0-51-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/pro
...
...
john@ubuntu:~$ On the server, I can see the connection appears as from the local subnet
john@ubuntu:~$ w
12:03:19 up 3 days, 19:53, 1 user, load average: 0.40, 0.11, 0.03
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
john 10.8.0.2 12:00 1:33 0.00s ? sshd: john [priv]Conclusion
I’ve now successfully connected a client to the OpenVPN server. The connection offers basic point to point connectivity at this point, meaning the server and client appear to be in the same subnet.

