Websites
Some very handy websites for IP discovery and DNS:
- https://www.dnscheck.tools – clean page that tells you your ip address and checks which DNS Servers you use. It checks that your DNS are authenticated with DNSSEC too.
- https://whatismyipaddress.com – tells you your public IP… with lots of ads.
- https://dnsleaktest.com – simple page that checks your public IP and also checks for DNS leaks
Other bits and bobs:
- I used https://lucid.app/ for drawing the network diagrams
Books
- IBM have a very comprehensive book on networks and routing. This is very comprehensive- not for the faint hearted.
Tools
Dig
Tool for looking up DNS entries.
john@ubuntu:~$ dig google.com
; <<>> DiG 9.18.30-0ubuntu0.24.04.2-Ubuntu <<>> google.com
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 49676
;; flags: qr rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 1
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 65494
;; QUESTION SECTION:
;google.com. IN A
;; ANSWER SECTION:
google.com. 110 IN A 142.250.186.142
;; Query time: 12 msec
;; SERVER: 127.0.0.53#53(127.0.0.53) (UDP)
;; WHEN: Wed Mar 05 16:05:44 UTC 2025
;; MSG SIZE rcvd: 55
The @x.x.x.x can be used to specify the DNS server
john@ubuntu:~$ dig @1.1.1.1 google.com
; <<>> DiG 9.18.30-0ubuntu0.24.04.2-Ubuntu <<>> @1.1.1.1 google.com
; (1 server found)
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 10682
;; flags: qr rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 1
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 1232
;; QUESTION SECTION:
;google.com. IN A
;; ANSWER SECTION:
google.com. 223 IN A 142.250.180.110
;; Query time: 2 msec
;; SERVER: 1.1.1.1#53(1.1.1.1) (UDP)
;; WHEN: Wed Mar 05 16:06:04 UTC 2025
;; MSG SIZE rcvd: 55
In each of the responses above you can see the SERVER section gives the IP of the DNS server. In the first case the IP of 127.0.0.53 indicates a local resolver is running.
Route
If you want to tell how your Mac is sending traffic, the route command will show you interface the request is sent over.
(base) 9:47:john@rizzo2:/Users/john route get 1.1.1.1
route to: one.one.one.one
destination: one.one.one.one
gateway: 10.8.0.1
interface: utun8
flags: <UP,GATEWAY,HOST,DONE,WASCLONED,IFSCOPE,IFREF,GLOBAL>
recvpipe sendpipe ssthresh rtt,msec rttvar hopcount mtu expire
0 0 0 31 6 0 1500 0
(base) 9:48:john@rizzo2:/Users/john
Another example – this will show the “default route” to the internet
(base) 10:04:john@rizzo2:/Users/john route -n get 0.0.0.0
route to: default
destination: default
mask: default
gateway: 192.168.1.254
interface: en12
flags: <UP,GATEWAY,DONE,STATIC,PRCLONING,GLOBAL>
recvpipe sendpipe ssthresh rtt,msec rttvar hopcount mtu expire
0 0 0 0 0 0 1500 0netstat
to check the routing table on you mac
(base) 10:29:john@rizzo2:/Users/john netstat -rn
Routing tables
Internet:
Destination Gateway Flags Netif Expire
0/1 10.8.0.1 UGScg utun8
default 192.168.1.254 UGScg en12
10.8/24 10.8.0.2 UGSc utun8
10.8.0.2 10.8.0.2 UH utun8
127 127.0.0.1 UCS lo0
DNSTop
DNS Top is a tool that lets you see the DNS requests travelling out/in on a network interface. The project homepage can be found at http://dns.measurement-factory.com/tools/dnstop/index.html
It can be installed via apt on ubuntu
john@ubuntu:~$ sudo apt-get install dnstopIt can be installed on Mac with
11:22:john@rizzo2:/Users/john brew install dnstopWhen you run it, you specify the interface you want to monitor. For the VPN traffic, we use tun0 as the interface name
john@ubuntu:~$ sudo dnstop tun0Press 2 (e.g. the number 2 on your keyboard) to see the requests coming in – this is great when you use it with a tool like dig, as you can actually see the DNS request coming in.
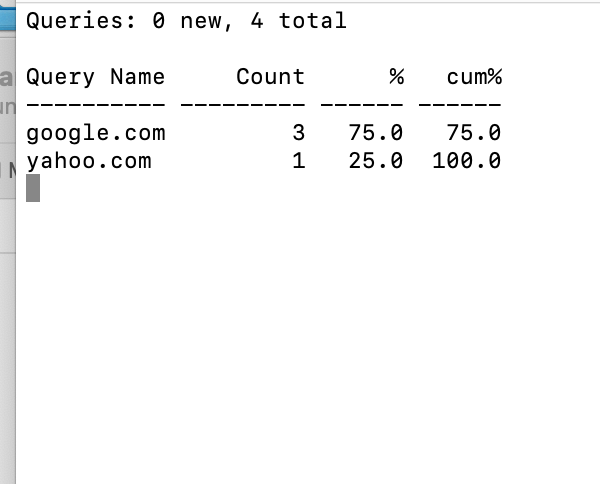
If you leave it running while you work, you can see all of the background chatter as services lookup addresses
To reset the counters press CTRL-R
To exit press CTRL-X
If you have it running on the VPN server prior to connecting (on screen 2) then when you connect you’ll see a spike in traffic as soon as you connect. If you simultaneously have it running on your local machine on your regular network interface you will see the count of requests stays static – e.g. all of the dns request are being sent out over the VPN. When you disconnect the VPN the local dnstop will show a spike and the VPN server dnstop will show no more updates – showing the DNS requests are going out over the local interface as expected.

